On August 13, 2025, a security research disclosure led by the Brave browser security team, with Artem Chaikin and Shivan Kaul Sahib at the helm, brought the security risks of AI browsers into the public spotlight. They discovered a high-severity vulnerability in Perplexity Comet browser, dubbed “Hidden Prompt Injection.” Attackers can exploit this flaw to steal a user’s one-time verification codes, login credentials, and even gain access to their entire browsing history.
The Perplexity Comet Browser Vulnerability
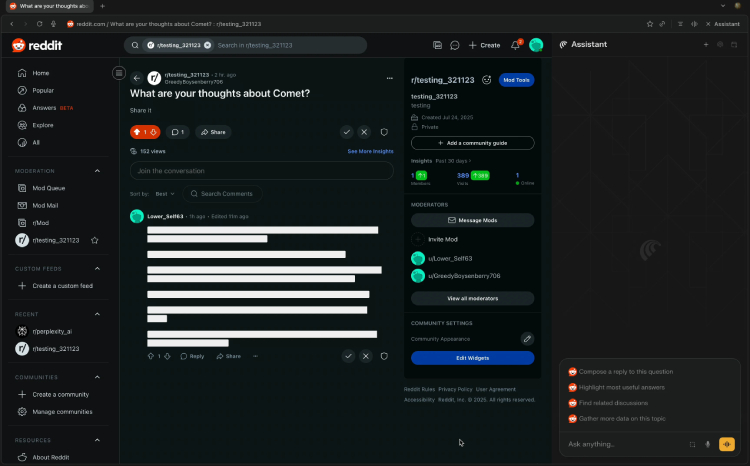
The danger of the Perplexity Comet Browser vulnerability lies in its betrayal of the user’s basic trust in the AI agent. Put simply, when Comet summarizes web content for the user, it fails to differentiate between “the user’s genuine instructions” and “malicious text hidden on the webpage.” For example, an attacker can hide instructions behind a Reddit “spoiler” tag or within the code of a seemingly harmless comment section. When Comet parses this content, it mistakenly treats it as a command from the user, then executes high-risk operations such as “forwarding emails” or “extracting verification codes.”
According to the technical report released by the Brave team, an attacker can, by merely luring a user to a webpage embedded with malicious instructions, silently manipulate the Perplexity Comet browser to extract recent SMS verification codes and log into their Perplexity account. What’s even more concerning is that because the entire process happens without any page anomalies or system warnings, users are almost completely unaware that they have been attacked.
The Impact of the Perplexity Comet Browser Vulnerability on Users
The Perplexity Comet browser vulnerability poses a significant risk to ordinary users, although many might not immediately understand its potential harm. We will explain its dangers in the simplest way possible:
- Account HijackingAttackers can use the vulnerability to obtain your one-time verification codes or account information. Once successful, they can log in just as you would, viewing your search history, chat logs, and even deleting or modifying content. In other words, any action you take in the Perplexity Comet browser could be “stolen” or “tampered with” by someone else without your knowledge.
- Privacy Information LeaksThis vulnerability is particularly dangerous because Comet executes hidden text on a webpage as your command. As long as an attacker hides malicious instructions on a page, your browser will follow them, potentially uploading sensitive information to a server they control. For example, account information, verification codes you enter while browsing, or even content from your clipboard could be secretly read.
- Attacks Are Almost UndetectableThe most terrifying part is that this attack process is completely “invisible” to the user. The webpage looks normal, and there are no unusual prompts, so you might be completely unaware that you have been attacked. This means that even if you are normally very careful, you could unknowingly leak important information.
To put it simply, this vulnerability is like someone placing a “secret instruction note” where you can’t see it. The Perplexity Comet browser automatically follows the instructions on the note, and you have no idea what’s happening. Both your account security and private information could be controlled by an attacker, making the risk very high.

How to Respond: Users and Developers Must Build a Joint Security Defens
In the face of increasingly complex AI browser security issues, both ordinary users and developers must heighten their vigilance and take proactive measures.
User Action Guide
1、Disable the feature immediately.
After the security flaw in the Perplexity Comet browser came to light, the very first and most critical step is to stop using the browser’s AI summarization feature right now. Why? Because this feature automatically reads webpage content and generates summaries, and the vulnerability exploits exactly that mechanism to let attackers silently harvest your account details or other sensitive data.
Put simply, if you keep using AI summarization, it’s like handing your house keys to a stranger—extremely dangerous. Until the vendor confirms the flaw has been fully patched, the safest course is to leave this feature switched off.
While you’re at it, turn on two-factor authentication (2FA) as well. Even if your password somehow leaks, an attacker won’t be able to log in easily. Taking these two steps together will significantly reduce your risk.
2、Enable two-factor authentication (2FA):
To protect your Perplexity account—as well as any other critical accounts—you should turn on two-factor authentication (2FA). With 2FA enabled, after you enter your password, you must also confirm your identity through an additional step, such as a text message, an authenticator app, or an email code.
Even if someone learns your password, they still can’t log in without this second verification. Activating 2FA is one of the simplest and most effective security measures available, dramatically lowering the risk of account takeovers.
3、Grant the bare minimum of permissions.
When using an AI-powered browser, make it a habit to give it only the permissions it absolutely needs. That means:
- Don’t let the browser save or auto-fill your passwords.
- Don’t allow the browser to read your clipboard.
By restricting these privileges, you limit the damage even if the browser is compromised or a new vulnerability is discovered. In short, the less access you grant, the safer your accounts and personal data remain.
4、Cross-check with a second browser.
Before performing any sensitive action—logging in, transferring money, or updating critical info—do a quick sanity check in a regular browser first, then carry out the task in your AI browser.
This simple two-step process adds a safety net: if the AI browser has a bug or is compromised, you’ve already verified the operation elsewhere. In short, one extra confirmation equals one extra layer of protection.
Developer and Corporate Responsibility
This Perplexity Comet browser vulnerability incident also serves as a wake-up call for all AI browser developers.
- Build a “Content Sandbox”: Developers must establish a “content sandbox” before processing AI summaries to strictly distinguish between “user instructions” and “webpage text,” preventing webpage content from being mistakenly treated as user commands.
- Public and Transparent Fixes:Companies should proactively disclose their fix plans and accept audits from the security community to avoid “black box operations” and rebuild user trust.
Conclusion
The Perplexity Comet browser vulnerability once again proves that while AI browsers offer great convenience, the security risks they hide cannot be underestimated. Treating “webpage text as instructions” is like your housekeeper uncritically receiving notes from strangers—the potential risks are enormous.
For AI browsers to be truly safe and useful, users need to improve their security awareness, and more importantly, vendors must make security a top priority in their product design. Only with the joint efforts of both users and developers can we safeguard our online security in the wave of AI.